Features
Process
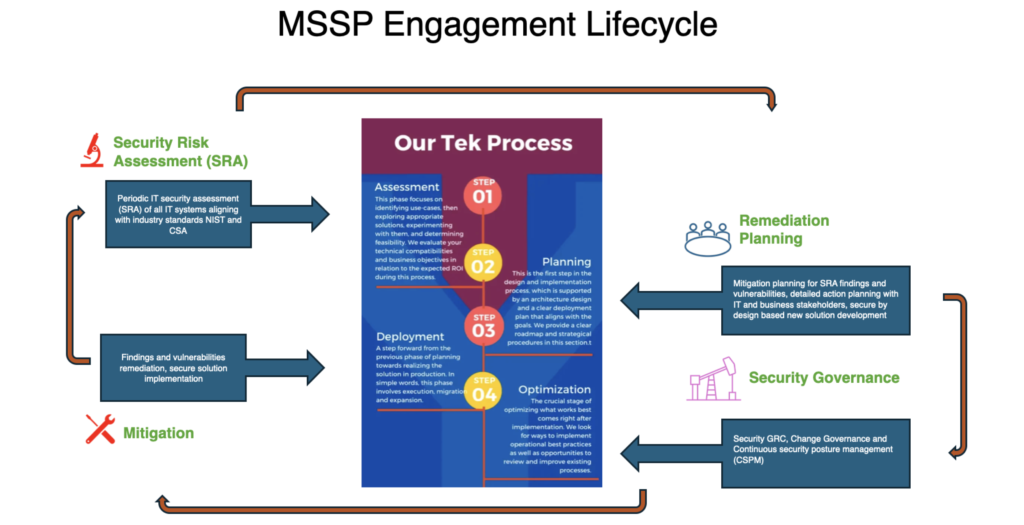
The MSSP Engagement Lifecycle includes Security Risk Assessment (SRA), Mitigation, Remediation Planning, and Security Governance to identify, resolve, and manage IT vulnerabilities. The core Tek Process involves Assessment, Planning, Deployment, and Optimization for seamless implementation. It ensures continuous security improvement and alignment with business goals, with our dedicated CISO team supporting you every step of the way.
Third-Party Security Risk Management Program (TPRM)
- TY provides comprehensive TPRM in performing security risk assessments of nth-party supplies for the enterprise as well as our clientele.
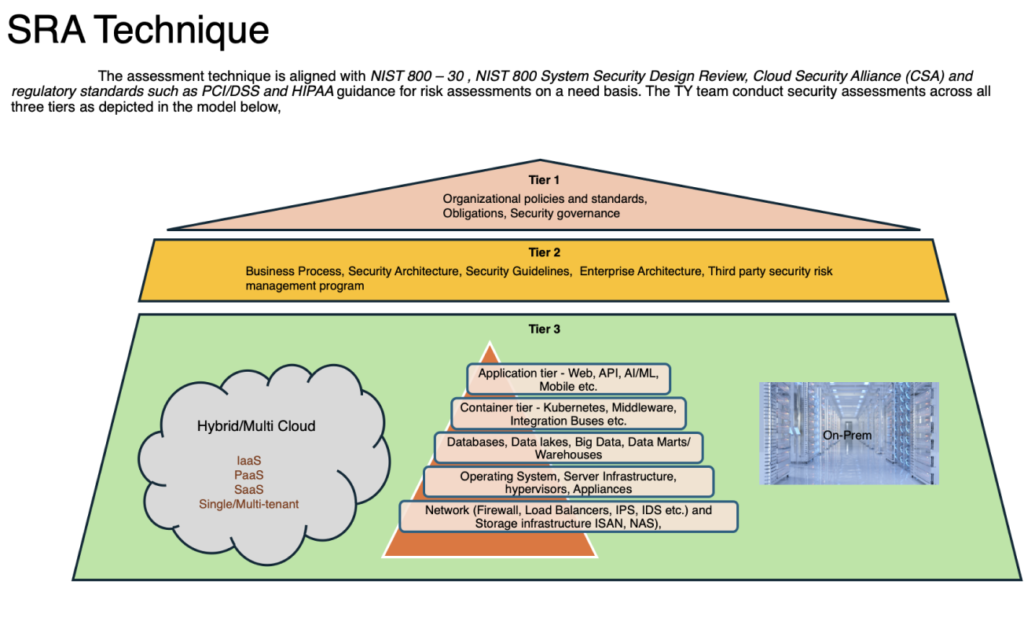
- The methodology is akin to the Enterprise SRA methodology and tailored to suit the nth-party’s IT infrastructure across all tiers.
- TY conducts the assessments utilizing home grown assessment tools/products aligning with the NIST 800 security assessment guidance, the CSA CAIQ, CIS Benchmarks, NIST AI RMF and regulatory frameworks such as HITRUST, FEDRAMP and PCI DSS as required on a case-by-case basis.
- TY will leverage Artificial Intelligence (AI)/Machine Learning (ML) powered data analytics, algorithms and data visualization capabilities to consolidate assessment data from customer native Cloud Security Posture Management (CSPM), Cloud Native Application Protection Platform (CNAPP), SaaS Security Posture Management (SSPM), Cloud Access Security Broker (CASB), Threat Intelligence systems, End Point Detection and Response systems (EDR), Security Information and Event Monitoring System (SIEM), Security Orchestration Automation and Response (SOAR) system by integrating customer feeds from the above systems into TY’s data aggregation, data analytics and visualization capability.
- The TPRM assessment will produce a qualitative and quantitative risk assessment of the supplier that includes business impact analysis and total cost of ownership of the risk.
- TY will continue to periodically assess the supplier for the customer on a yearly basis to refresh the residual risk rating.
- TY will also assist with and provide facilities/site inspections of suppliers on a need basis in order to complete the SRA.
- TY has extensive experience and has offshore facilities that can help provide offshore geolocation SRA of suppliers and will utilize the UN ITU Global Cybersecurity Index (GCI) as a key input.
- TY will engage the legal counsel for legal and privacy consultations as needed for the TPRM program.
- The future state of TY is to utilize a combination of home-grown and COTS AI/ML powered TPRM automated assessment products and the TY R&D initiatives are aimed at developing this capability, customers interested in the benefits associated with automating the TPRM program can provide valuable input to the R&D effort and participate in the pilot program
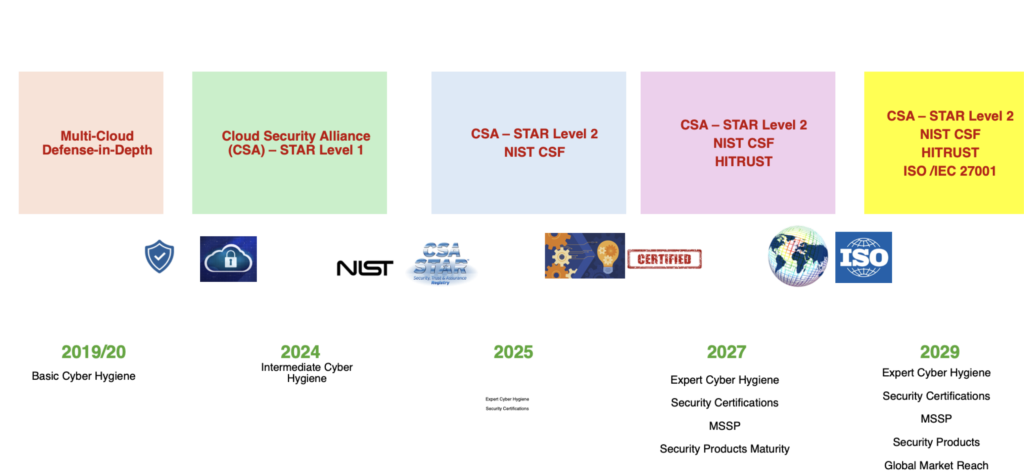
Tek Yantra Information Security Journey